The evolution of crypto bridge security tells two stories.
The first – a cautionary tale, with nearly $2.9B lost to bridge hacks, shaking user confidence.
The second story – one of innovation and resilience – is still being written.
In 2024, Across processed $11.6B in bridge volume without a single security incident. This wasn't luck—it was by design. While some other bridges are still vulnerable to bridging exploits, Across's unique architecture has proven that secure bridging at scale is possible.
This paradigm shift stems from a radical rethinking of bridge security. Rather than asking users to trust representative assets or validation mechanisms, we leverage an Intents-based architecture in which relayers—not users—take on the risk.
Here's how this approach is redefining bridge security.
Key Takeaways:
Across processed $11.6B in bridge volume in 2024 without a single security incident. This wasn't luck—it was by design.
Unlike traditional bridges that use wrapped tokens, Across exclusively uses canonical assets, eliminating entire classes of crypto bridge vulnerabilities.
Across shifts risk from users to relayers through an innovative Intents-based architecture where relayers compete to front capital for transfers.
The system remains secure through UMA's optimistic oracle, requiring only one honest participant.
The Bridge Security Crisis: Understanding What's At Stake
Before diving into how Across revolutionizes bridge security, let's examine the key vulnerabilities plaguing traditional bridges. Each represents a critical lesson in bridge architecture.
1. The Representative Asset Trap
Traditional crypto bridges ask users to trust "wrapped" or representative versions of their assets. When you bridge ETH, you typically receive a wrapped version like wrapped ETH. This introduces several critical risks:
Smart contract vulnerabilities can allow unlimited minting of these wrapped assets
Users must trust the bridge will honor redemptions of wrapped assets
If the bridge is compromised, wrapped assets can become worthless overnight
Real-World Example: In 2022, a hacker exploited a flaw in Wormhole Bridge’s contract’s verification steps. The attacker minted wrapped tokens without proper collateralization, making off with 120,000 wETH (worth over $320 million).
Across's Approach: Complete rejection of wrapped assets in favor of canonical assets only. When you bridge 1 ETH with Across, you receive 1 real ETH - not a wrapped representation.
New to crypto bridging? Check out our complete guide to crypto bridges
2. The Validator Vulnerability
Some other types of crypto bridges rely on a set of validators to approve transfers. This creates a centralized point of failure:
The Ronin bridge hack occurred when attackers compromised just five validator keys
Users must trust a small group of validators to act honestly
Validator collusion or compromise can lead to catastrophic losses
Real-World Example: In the Ronin Bridge hack of 2022, an attacker infiltrated Sky Mavis’s network to take control of five (out of nine) validators used to validate transactions for the Ronin network. This culminated in the loss of $624 million.
Across's Approach: Instead of traditional validators, we have built a competitive relayer network where economic incentives ensure security.
3. The Centralized Key Catastrophe
Many crypto bridges concentrate control in the hands of a small group of administrators or multi-sig holders. This centralization creates severe security risks:
The Harmony Bridge was compromised when just 2 out of 5 multi-sig holders were breached
Admin key compromise can lead to complete bridge failure
Users must trust that governance key holders will maintain perfect security
Centralized control contradicts web3's core principle of decentralization
Real-World Example: The Harmony Bridge hack of 2022 resulted from the compromise of two out of five private keys controlled by centralized operators.
Across's Approach: Decentralized security through UMA's optimistic oracle system, where any participant can flag malicious behavior, and economic incentives help maintain system integrity.
4. The Honeypot Problem
Traditional bridges must lock up user funds, creating massive honeypots that attract attackers. Consider:
Bridge smart contracts often hold billions in user funds
A single successful exploit can drain the entire pool
The larger the bridge grows, the more attractive it becomes to attackers
Real-World Example: The Multichain Bridge hack in 2023 led to unauthorized withdrawals of locked funds due to compromised private keys, with losses exceeding $125 million.
Across's Approach: There are no locked funds. Instead, relayers front capital for transfers, eliminating the honeypot risk.
5. The Messaging Mayhem
Many bridges rely on complex crosschain messaging systems that:
Are expensive due to high gas costs
Create delays waiting for message validation
Introduce new attack vectors through message manipulation
Real-World Example: The Alex Bridge suffered $4.3 million in losses due to a compromised deployer account during a contract upgrade.
Across's Approach: Intents-based architecture eliminates the need for complex messaging systems. Users simply express what they want to happen, and relayers compete to make it a reality.
How Across Reinvents Bridge Security
Traditional bridges ask users to accept significant risks: wrapped assets that could fail, validators that could be compromised, or massive honeypots that attract attackers. Across takes a radically different approach - one where users never have to compromise on security.
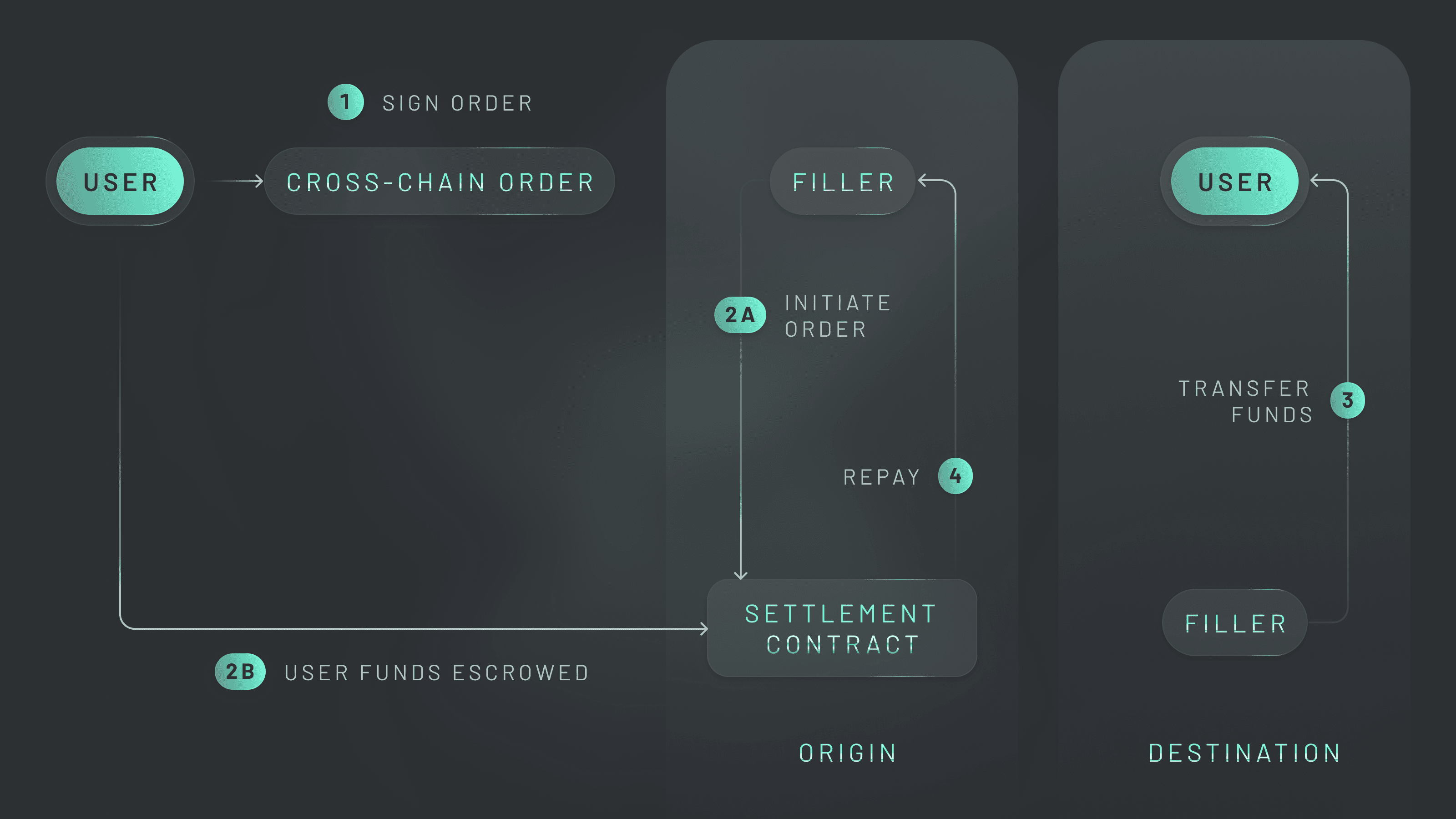
ERC-7683 provides a universal standard for crosschain Intents across EVM chains.
The Canonical Asset Revolution
At Across, we're canonical asset maximalists. This isn't just a philosophy - it's a security imperative. Users who bridge through Across receive only genuine, canonical assets on the destination chain. This means when you bridge ETH, you get real ETH - not a wrapped version that could be compromised in a bridge exploit.
By avoiding wrapped tokens entirely, we remove the risk of minting exploits and bridge-specific token failures. Users only need to trust the underlying blockchain, not additional bridge tokens or validation mechanisms.
The Relayer Risk Shift
Instead of forcing users to take on risk, Across's innovative relayer network fundamentally transforms the bridge security model.
Our relayers compete to provide the fastest and cheapest service while fronting their capital for transfers. This competition creates a decentralized, market-driven security model where relayers - not users - take on finality risk in exchange for modest fees.
Fierce competition among relayers keeps fees low while maintaining robust security, and our batched repayment system optimizes gas costs for everyone involved.
The Optimistic Oracle Advantage
Across is secured by UMA's optimistic oracle, creating a unique guarantee in the bridge ecosystem. The system enables any participant to flag malicious behavior, with economic incentives ensuring honest verification. This creates an environment where disputes are rare because bad actors stand to lose their stake.
Perhaps most importantly, the entire system remains secure as long as just one honest participant exists - a dramatic improvement over multi-sig systems that can fail if a few validators are compromised.
Fast Without Compromise
While other bridges force users to choose between speed and security, Across delivers both. Through our competitive relayer network, users enjoy instant transfers without sacrificing safety. Our optimistic verification system maintains security without imposing delays, and our batched settlement approach optimizes gas costs without compromising speed. The result is a bridge that's both faster and more secure than traditional alternatives.
Evaluating Bridge Security: A User's Guide
With billions in bridge volume moving daily across chains, choosing the right bridge isn't just about speed or cost - it's about protecting your assets.
Here's what to look for when evaluating bridge security:
Key Questions to Ask
Asset Type: Does the bridge use canonical assets or ask you to trust wrapped tokens?
Risk Model: Who actually bears the risk during the transfer - you or the bridge protocol?
Verification Method: How are transfers validated, and what security guarantees protect your funds? Optimistic verification or others
Track Record: Has the bridge demonstrated security at scale with significant volume?
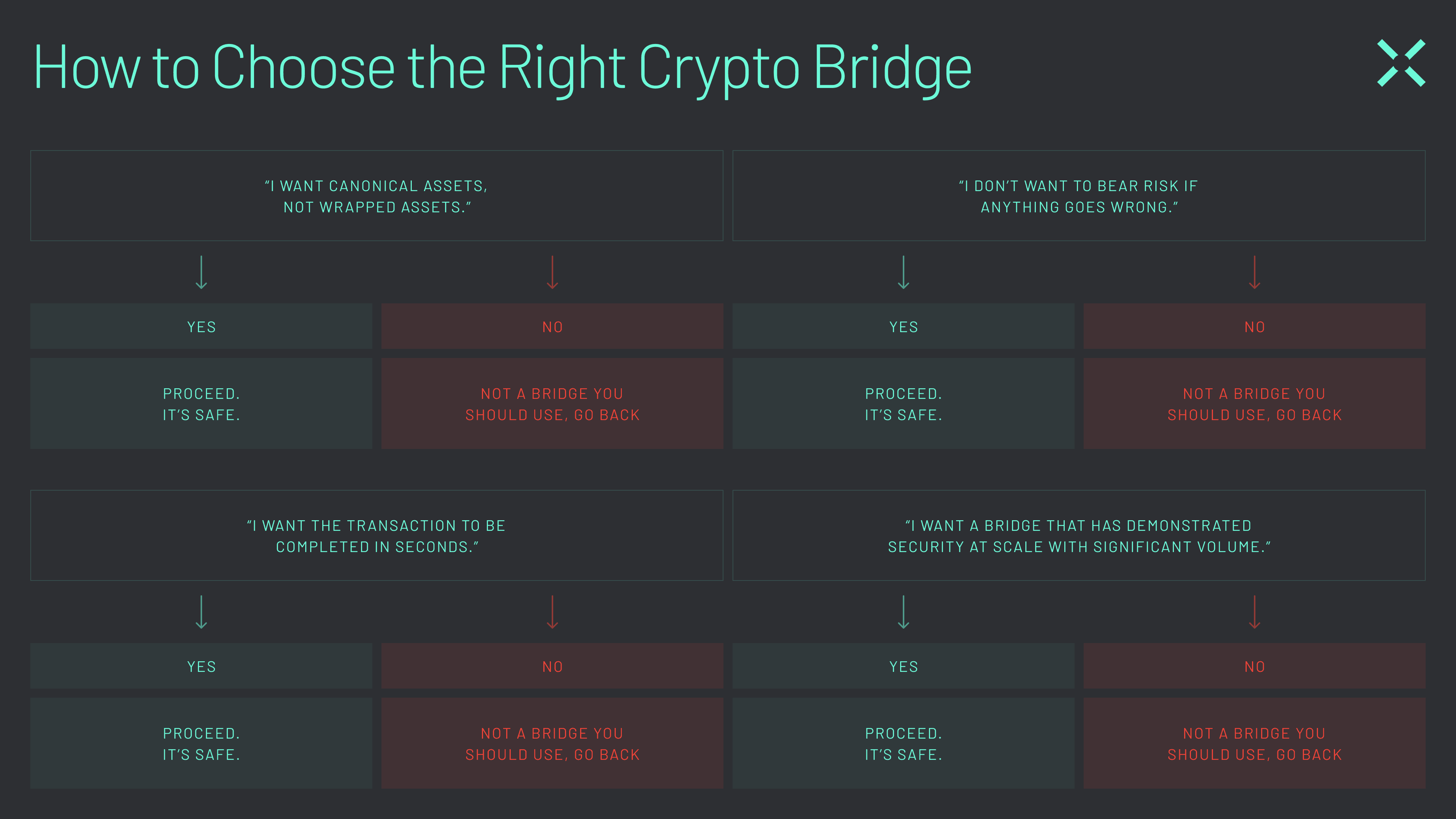
Questions to ask before using a crypto bridge
Across answers these questions through verifiable technical architecture rather than marketing promises. Users receive canonical assets, relayers bear transfer risk, and the system remains secure with just one honest participant in the network.
For Developers
If you're building crosschain applications, bridge security becomes even more critical. Your users' security depends on your bridge choice. Across offers:
Native crosschain hooks for protocol actions
Integration with crosschain intents through ERC-7683
Unified filler network for efficient execution
Settlement layer that prioritizes security without sacrificing speed
Beyond Security Features: Why Architecture Matters
The crypto community cannot become desensitized to bridge hacks. We can’t accept multi-million dollar exploits as inevitable risks of crosschain operations. Accepting such vulnerability isn't just dangerous - it's unnecessary.
A safer crosschain ecosystem is possible, but it requires rethinking bridge architecture from the ground up. This is where Across' layered approach proves its value:
Security by Design, Not Afterthought
Traditional bridges often add security features after their core architecture is established. Across takes the opposite approach - security principles shape every aspect of the system:
Canonical Asset Foundation: Using only real, native assets removes entire classes of vulnerabilities
Economic Security: Relayer competition creates natural security through market dynamics
Optimistic Verification: UMA's optimistic oracle provides a decentralized security layer that gets stronger as the network grows
Where Speed Meets Safety
The old belief that security requires sacrificing performance doesn't hold with modern bridging architecture. Across demonstrates this through:
2-Second Transfers: 99% of L2 transactions under $10,000 are filled in 2 seconds
Efficient Gas Usage: Batched repayments and optimized relayer systems minimize costs
Competitive Execution: Relayer competition drives both security and performance
User Experience as a Security Feature
The most secure bridge is the one that people can use confidently and correctly. Across's user-first design includes:
Intents-Based Operations: Users express what they want, and the system handles the complexity
Developer Empowerment: Simple integration that preserves security guarantees
Full Transparency: Open documentation and rigorous auditing prove security claims
This combination of architectural innovation, performance optimization, and user-centric design creates something unique in the bridge ecosystem - a more secure and usable solution than traditional alternatives.
Building a More Secure Crosschain Future
The history of bridge security has been written in lost funds and compromised assets. But with Across, a new chapter is being written - one where security doesn't require compromise.
In 2024, Across demonstrated this new paradigm at scale:
$11.6B in secure bridge volume
8.3M transfers without security incidents
2-second transfer times while maintaining security guarantees
Over 400K monthly active wallets trusting the system
This isn't just about building a better bridge - it's about establishing the foundation for a truly interoperable Web3. Through canonical assets, intent-based architecture, and decentralized validation, Across is proving that cross-chain interactions can be as secure as they are seamless.
Ready to Experience Secure Crypto Bridging?
For Users:
Join our community discussions about bridge security at Discord
For Developers:
Explore our integration guides at docs.across.to
Learn more about crosschain Intents with ERC-7683
The future of crosschain interaction doesn't have to be defined by security compromises. It can be - and with Across, already is - defined by security guarantees.